This is another Wi-Fi security standard that has been introduced to prevent passive eavesdropping especially in public spaces that uses open authentication. OWE capable client device is unaware of the security procedure that is implemented in the background.
OWE uses embedded DF key exchange during the association to generate PMK, followed by 4-way handshake. End to end security is not implemented in OWE where the identity of the end-users are not verified. It mandates the use of PMF to prevent MITM attacks since end-users are not verified.

OWE-transition mode is used to allow all the devices that supports/not supports OWE to connect a single SSID. If a non-OWE capable client connects to OWE SSID, then it continues as a regular open authentication. However, the OWE capable wireless client will be connected to the hidden BSSID that has been automatically created for the same essid to proceed with the embedded DH association process.
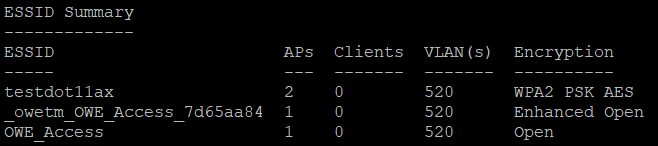
In the below example, the actual SSID created for OWE is “OWE_Access” that automatically creates a hidden SSID : “_owetm_OWE_Access_7d65aa84”.
Packet captures show additional IE : Wi-Fi Alliance OWE Transition mode in the beacon and OWE Diffie-Hellmann parameter in the Assoc exchanges for the OWE client device.
Below test has bee performed with OWE capable android Client device: 98:f6:21:2d:57:81 connected to the OWE Aruba AP in channel 48E.
OWE Beacon
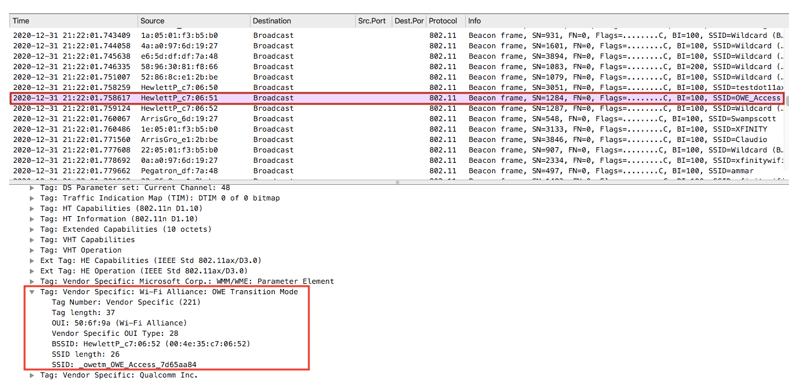
OWE Beacon
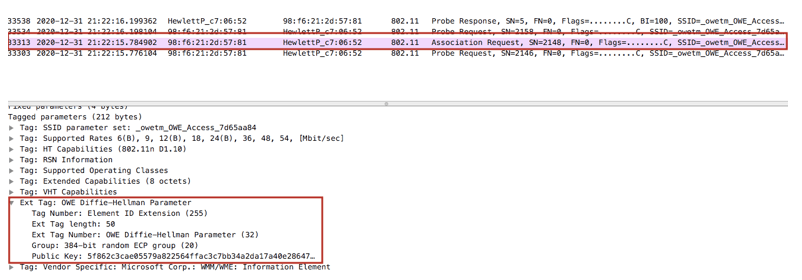
OWE Probe Req/Resp

OWE Probe Req/Response
OWE Assoc Request
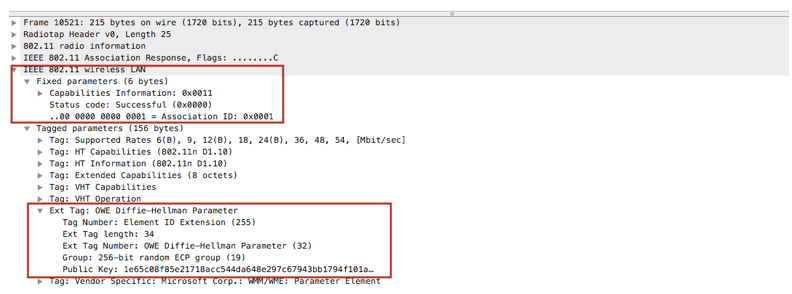
OWE Assoc Response – failed

OWE Assoc Response – Success
Below link shows few OWE supported Intel Wireless adapters:
https://www.intel.com/content/www/us/en/support/articles/000057519/network-and-io.html
References:
CWSP – 206 Official Study Guide