WPA3-Personal (or WPA3-SAE) can be implemented in two modes: WPA3-SAE-transition mode that allows both WPA2 and WPA3 devices to use the same passphrase to connect to the wireless network. PMF is only optional in this case to allow the WPA2 clients to connect. However, PMF is mandatory in WPA3-SAE mode and is required for all 802.11ax to support this mode.
In WPA3-SAE mode, even if the attacker accesses the network using the passphrase, they will still not be able to decrypt the user traffic. This passphrase is only an index on the elliptical curve graph to generate cryptography to form the PMK. Using SAE and ECC (elliptical Curve Cryptography), WPA3-Personal is made secure. More details are covered in the “Evolution of Wireless Encryption standards” post.
Below is the capture taken for a client- 98:f6:21:2d:57:81 connected to Aruba wireless network in WPA3-SAE mode.
Beacon –Advertising SAE capability in RSN IE under AKM along with PMF support in RSN capabilities.

Probe Response – Similar to beacon showing SAE and PMF support in RSN IE. Please note that RSN IE is not a part of the probe request frame and hence not shown here.

Authentication: Probe Req/Response frames are followed by 4 Auth frames.
SAE Commit from the client
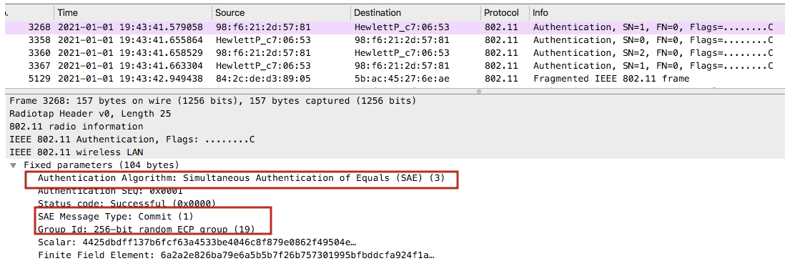
SAE Commit from the AP
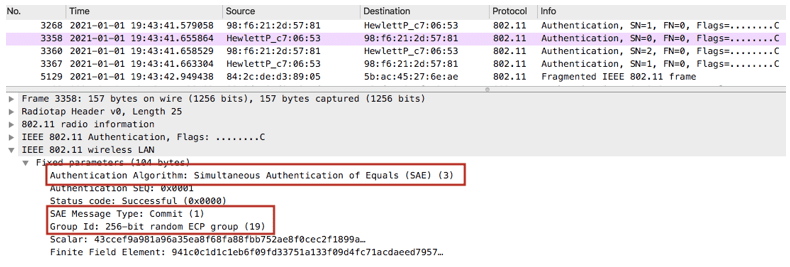
SAE Confirm from the client
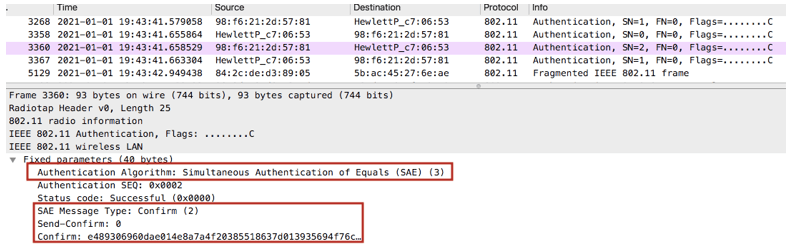
SAE Confirm from the AP
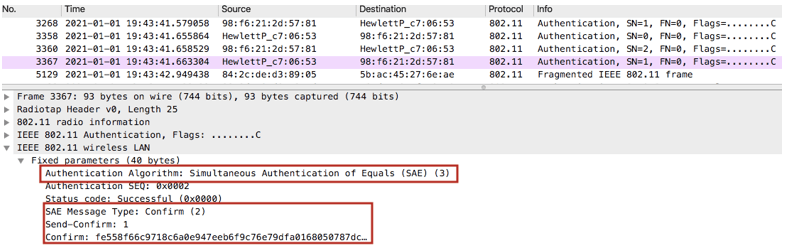
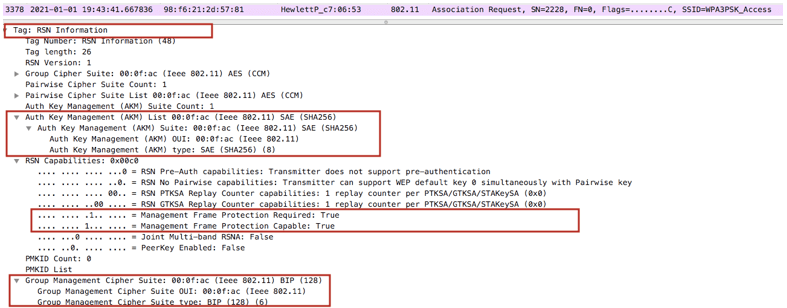
Assoc Request – This is the frame where the client shows its SAE capability and PMF support in it’s RSN IE.
Assoc Response
References:
CWSP-206 Official Study Guide