Dot1x authentication is a widely used secure authentication mechanism after the association of the wireless clients to the Wi-fi network in most of the enterprises. There are 3 main components involved in this process: Supplicant, Authenticator and Authentication Server (AS).
Supplicant – software running on the wireless client device that supports 802.1x authentication.
Authenticator can be the WLC or AP that acts as the mediator between Supplicant and AS. Communication between the supplicant and AS does not happen directly and has to pass through this mediator.
Authentication Server is an AAA server that is capable of performing authentication, authorization and accounting functions. Authentication validates the identity of the data source, authorization provides the authenticated client with appropriate network access and accounting keeps track of the session details like login and logout time for the valid users.
All the communications between the Supplicant and Authenticator occurs via EAP protocol and RADIUS protocol is used for data exchange between Authenticator and AS. Any EAP message going from Authenticator to the Supplicant is called EAP Request and the response message that comes back from the Supplicant to the Authenticator is the EAP Response. Similarly, the message that goes from Authenticator to the AS is called RADIUS Access Request and the response back is the RADIUS Response. The two main purposes of a Dot1x Authentication is 1. Validate the client user identity 2. Generation of PMK (Pairwise master key).
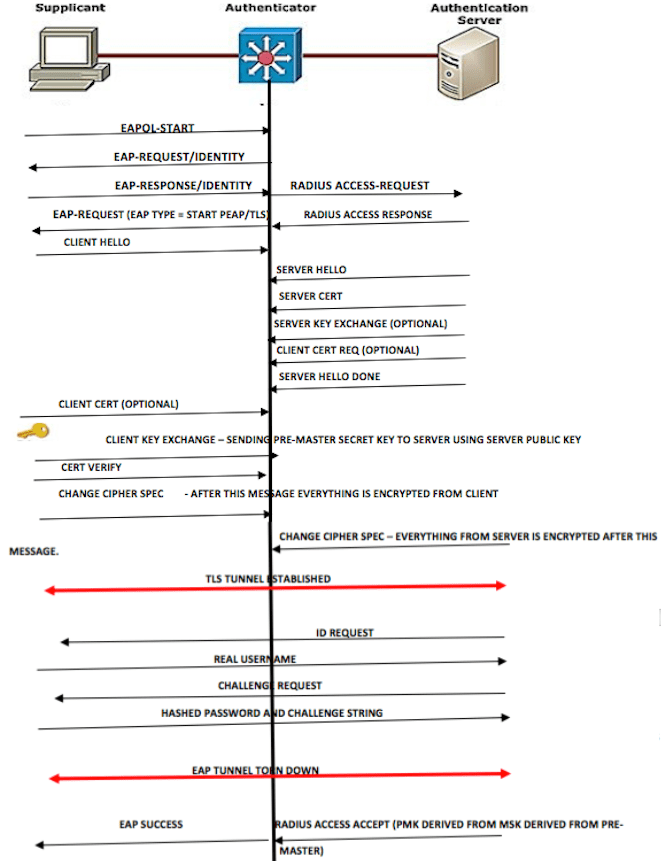
The above is the packet flow for EAP-PEAPV0 (MSCHAPV2) or EAP-TLS of 802.1x authentication. This process begins with an optional EAP-START message from the supplicant followed by EAP-ID request from the authenticator or starts with EAP-ID request from the authenticator. Supplicant can either provide the actual user name or false user identity to WLC/AP, which in turn sends this to the AS as radius access request. RAD server sends back Radius response informing the supplicant to start the outer EAP tunnel formation with the EAP type. This is SSL tunnel using server and client handshake, certificates and key exchange. Please refer the post “understanding SSL” to get better clarity on the ssl handshake process. EAP-TLS process end with TLS tunnel establishment and then followed by EAP-SUCCESS step. However, EAP-PEAPV0(MSCHAPV2) will use the entire packet flow described above.
802.11i Key Management – Dynamic session key generation with 4 way handshake
Once Dot1x authentication completes successfully where the supplicant and the authenticator acquires PMK, dot11i process starts with the aim to create two important keys: PTK (Pairwise Transient key)for encrypting unicast data traffic and GTK (Group wise transient key )for encrypting multicast traffic by the exchange of EAPOL-KEY messages.
PTK is generated by a pseudo random function using PMK, SNONCE, ANONCE, SMAC, AMAC.

ANONCE – Random integer generated by AP
SNONCE – Random integer from the supplicant
PTK is a combination of KCK (confirmation key), KEK (Encryption key) and TK (Temporal Key), 128 bits each
KCK – used for construction MIC for data integrity during 4-way handshake
KEK – used for encrypting GTK
TK – used for Data encryption
References:
- CWSP Official Study Guide